Relevant Products
External authentication is available in pro print pro mfp
SAFEQ Cloud supports external authentication provider where external authentication service such as External Card Repository is used to identify users from different authentication providers. For more details on how a specific external provider works, see the documentation section dedicated to that external provider.
Adding a new external authentication provider
To add a new external authentication provider, perform the following steps:
-
Log in to SAFEQ Cloud Web UI and go to Users page and Authentication providers tab.
-
Click Add.
-
Fill in the following:
-
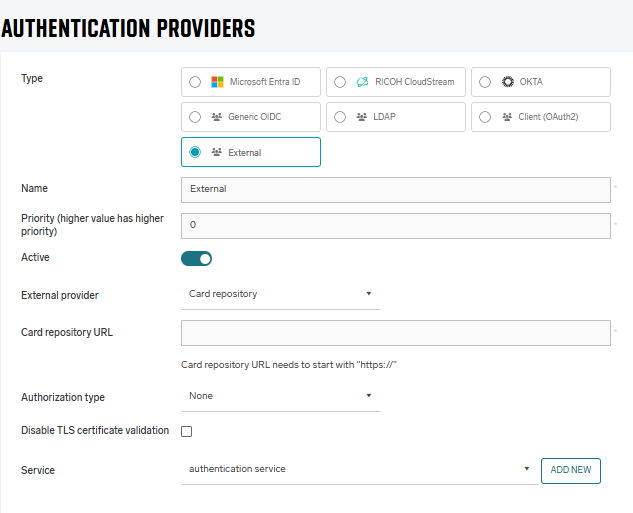
Type – select External.
-
Name – Name your new authentication provider. Should be prefilled with selected Type.
-
Priority – A number determining the order in which authentication providers will be called until one succeeds. Higher-priority providers will be called first.
When authenticating via card/PIN (Short ID), the user's card/PIN is first searched for in SAFEQ Cloud and only if it is not found, the authentication providers are called in order of their priorities. This means that when using External Card Repository (ECR) and the user has a card assigned in SAFEQ Cloud, they are authenticated without a call to ECR. If you want to call the ECR for every card authentication request, do not assign cards to users in SAFEQ Cloud.
-
External provider – select the external provider.
-
Service – Select the authentication service. If no service is already created, you can add it via the Add button. If the primary server has only one authentication service, or if only one authentication service in general exists, it is pre-selected by default.
When a user is authenticated using ECR, they will be created in SAFEQ Cloud database under the corresponding Client provider and visible in the Users section, when you choose the corresponding Client provider in the drop-down list.
User properties and Access Control can be modified by administrators.
-
External Card Repository (ECR)
-
In the External provider, choose Card Repository.
-
Fill in the following information:
-
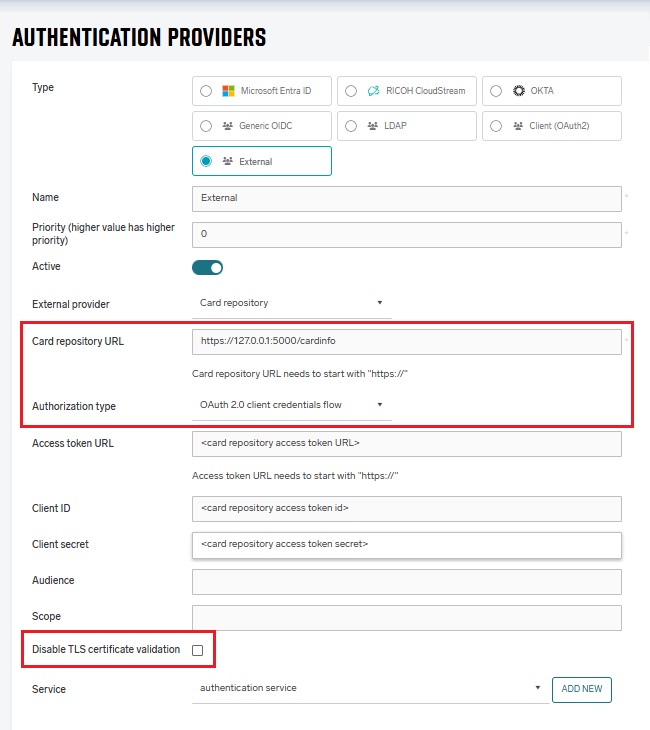
Card repository URL – The URL of the External Card Repository.
-
Authorization type – the authorization that is used for securing the ECR. Currently, SAFEQ Cloud supports only ECR that is secured using OAuth 2.0 Client Credentials Flow or not secured:
-
OAuth 2.0 Client Credentials Flow – The recommended option used to authenticate requests from SAFEQ Cloud to ECR.
-
None – We strongly recommend not to use unsecured ECR outside of scenarios where both SAFEQ Cloud and ECR are deployed within the customer's LAN.
-
-
Disable TLS certificate validation – The option to disable validation of HTTPS certificates. We strongly recommend keeping this option disabled and always validating certificates.
-
Service – Select the authentication service. If no service is already created, you can add it via the Add button.
-
-
-
If you selected the OAuth 2.0 Client Credentials Flow, fill in the following information:
-
Access Token URL – A mandatory field. The URL where SAFEQ Cloud can request an access token.
-
Client ID – A mandatory field. The Client ID that SAFEQ Cloud will use to get an access token from the ECR.
-
Client Secret – A mandatory field. The Client secret that SAFEQ Cloud will use to get an access token from the ECR.
-
Audience – An optional field that you can use to restrict the usage of the access token.
-
Scope – An optional field which specifies the scope of the access token.
-
User expiration policy
A user who authenticates at the MFD via an External provider will automatically get an expiration value from the user detail. The default value is one hour, unless it is set otherwise in the external provider.
This means that after the defined time since authentication via an External provider (e.g. one hour), the user won’t be able to authenticate at MFD via less secure means, such as Short ID (PIN). The user must authenticate in a secure way, such as card number stored in ECR, username/password, or OIDC (for example, via SAFEQ Cloud Client). In this way, the token is refreshed, and the user expiration starts running again.
For more details, see External Card Repository.
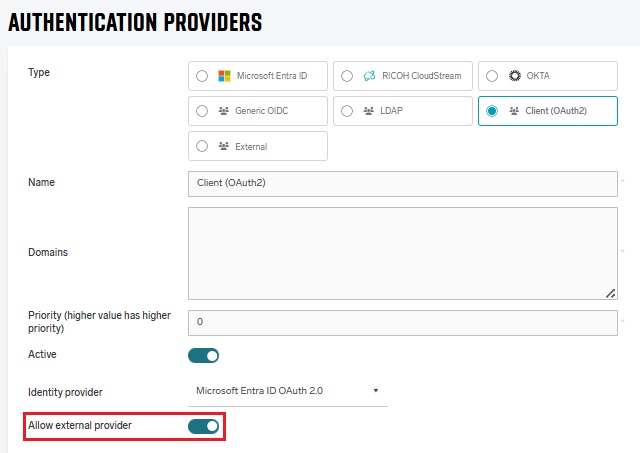
Enabling external authentication for a client provider
External authentication must be allowed in each provider where the users will be logging via external authentication. External authentication is only supported for authentication providers where Type is Client. To allow external authentication in your client provider, click Show advanced options, and then select Allow external provider.