Relevant Products
Client-side authentication is available in pro print pro mfp
To use Google Workspace Client authentication, you must create a service account. This will allow you to validate users against Google and synchronize Groups for Access Control.
-
Follow the steps in Google documentation: https://developers.google.com/identity/protocols/oauth2/service-account#creatinganaccount.
-
As part of the key creation process, a private key is generated as a JSON file. Save it in your PC. You will need to copy its content into Secret JSON file content form field.
-
Delegate the service account that you have created for domain-wide authority. Follow the steps from Google documentation: https://developers.google.com/identity/protocols/oauth2/service-account#delegatingauthority .
-
You will need the following scopes for SAFEQ Cloud communication:
-
https://www.googleapis.com/auth/admin.directory.user.readonly
-
https://www.googleapis.com/auth/admin.directory.group.member.readonly
-
https://www.googleapis.com/auth/admin.directory.group.readonly
-
-
In the Google Workspace authentication provider form creation, enter the account name that has a super admin role (not service account name!) and paste the content of the JSON file you saved before. Make sure that the JSON file content is wrapped in curly braces { } when you paste it. Click Test to make sure it is working. You can also serialize JSON and paste it as a solid string in between { }.
This approach requires using admin account for service account to impersonate, the possible actions for this impersonation are limited by the scopes you entered for the domain-wide delegation. For more information, see this article by Google.
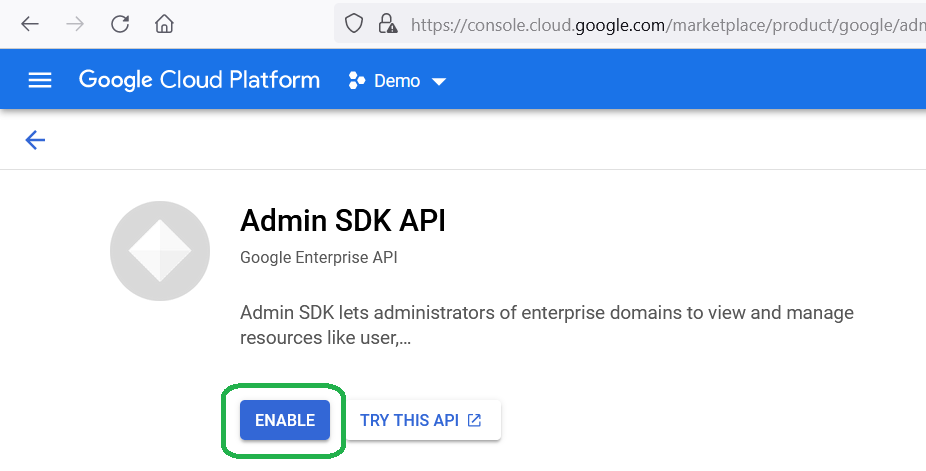
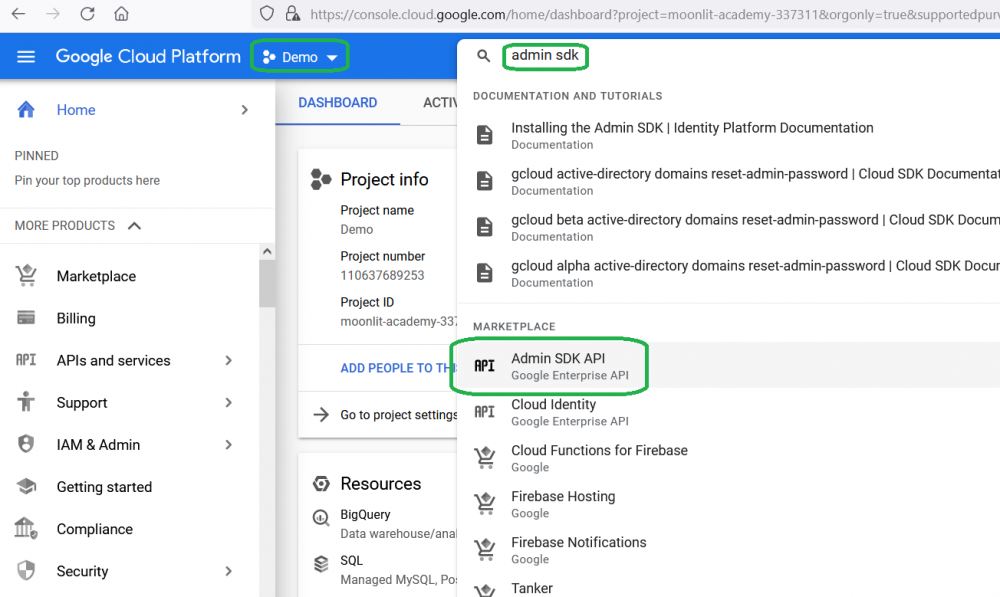
Check if Admin SDK API is enabled for your project, and if it’s not, enable it: choose your project and type in the search line “admin sdk”
if it is disabled, click Enable button