Relevant Products
Security and privacy are available in BREEZE PRINT BREEZE MFD PRO PRINT PRO MFD
Document Scope and Use
This document provides an overview of the security features and practices implemented in YSoft SAFEQ Cloud solution. Information contained in this document is intended to assist Y Soft partners and end customers in understanding how the security of the solution is ensured and how the end customers may leverage the security features of the solution to maintain the confidentiality, integrity, and availability of their data.
The target audience for this document includes IT professionals, security professionals, and decision-makers responsible for selecting and implementing print management solutions in their organizations. This document also provides insight into the security controls implemented by Y Soft to ensure compliance with relevant regulations and standards.
More details about Y Soft secure development practices and other security-related topics are available in the security w hitepaper: https://www.safeq.com/cloud-print-security-whitepaper
Y Soft Security and Risk Focus
Secure by design for both pure cloud and edge printing
SAFEQ Cloud service delivers cloud-based print, copy and scan services with optional edge components as per customer needs.
Y Soft and its Partners are jointly responsible for the security of their customers’ print infrastructure.
By utilizing optional Edge virtual appliances or physical devices, we stand by our commitment to privacy even when on-premise infrastructure is required by the customer. Document storage and processing remain local to maintain document integrity and privacy. Only the print job’s selected metadata travels encrypted to the cloud for management and reporting purposes. Document content remains secure because it never leaves your premises and thus never reaches cloud components. Data that is not present in the cloud cannot be externally compromised because they simply are not “there.”
Customers may choose to implement SAFEQ Cloud in either shared or reserved instances. In a reserved instance, the document processing and storage are dedicated to one customer, so data is never exposed to any other entity. Document content and user identity thus also remain secure.
How does it work
SAFEQ Cloud (software) is embedded on multifunction devices (MFDs) and printers at the customer's business location. There, it is either connected to a Y Soft Edge device, (hardware or virtual appliance) or directly to a cloud instance. The edge device is responsible for processing print jobs onsite. Even though it does the work of a server, the Edge device, much like a network router, is self-contained and needs no customer maintenance to perform its function – processing print jobs. A Virtual Appliance operates in a similar manner to the Edge hardware device but it runs on a customer-supplied server or virtual machine.
|
|
Zero Trust Infrastructure |
SAFEQ Cloud uses software-defined infrastructures in Cloud and Edge to provide auto-scaling and advanced networking and security. In Y Soft view of the Zero Trust approach, there are no trusted networks and zero implicit trust among services, instances, and clients. All system services, components, Edge devices, and (optionally) deployed MFDs are mutually authenticated, and all communication is secured using industry-standard protocols, such as TLS (Transport Layer Security) 1.3. Zero Trust is often perceived as a network-level architectural decision. Yet we believe that the Zero Trust approach needs to be applied holistically. SAFEQ Cloud service provides “beyond the network” Zero Trust capabilities, such as individual service recycling and tenant infrastructure recycling in multi-tenant environments.
The following network protocols are primarily used:
Communication happens in 3 tiers:
|
|---|---|---|
|
|
Zero Trust Secure Edge |
In the case of optional Edge components, Zero Trust must also be applied on Edge devices. Again, securing only the services/applications running on the Edge device is not enough. Y Soft approach to Secure Edge using the Zero Trust principles provides the following capabilities: Trusted and Secure Device Identity - Each device maintains a trusted bond with its associated cloud tenant for management. Such identity is sufficient for establishing trust and unique identification of the device. This identity includes but is not limited to, secure establishment and storage of encryption and digital signing keys in a specialized secure enclave on the device. Trusted Path - Y Soft secure Edge devices provide trusted boot and trust path capabilities, which ensure that only trusted operating system can be booted and run on the device. This ensures decreased (or zero) attack surface and customer privacy and data integrity protection. Mutual Service Authentication - Once secure cloud and edge environments are established, all services and devices (including optional authentication for MFDs – if supported by the MFD vendor) are performed using mTLS industry standard protocol. Cloud Manageability - All cloud and especially edge deployments are securely manageable from the cloud, including seamless remote deployments and rolling / transitional updates and upgrades. Device-to-Cloud communication is secure, including mutual authentication. Remote Wipe of Customer Data - All customer data hosted on Edge devices can be remotely wiped using the cloud management capabilities. |
|
Data transfer |
Print Job Data in transit: Workstation to Edge device & Edge device to the MFD |
Because the Edge device is secure in your trusted network, all print job data stays safely within your company’s boundaries. Data is transferred via secured IPPS protocol for printers that support higher levels of data security. Support for legacy, unsecured protocols, such as LPR is also available, yet disabled by default. |
|
|
Print Job Data in transit: Workstation to Cloud & Cloud to the MFD |
Data is transferred via secured TCP or HTTPS protocol to the cloud and downloaded from the cloud in the context of a user authenticated to the MFD. The MFD is trusted, using device-authenticated HTTPS protocol. |
|
|
Scan Job Data in transit: MFD to Edge/Cloud |
Scan data are transferred to cloud services using device-authenticated WebDAV/S or HTTPS protocols, with authentication tied to a specific user context. The choice between WebDAV/S and HTTPS depends on the device vendor, as different manufacturers may implement different transmission methods.
|
|
|
Scan Job Data in transit: Cloud to customer's email |
Scan data sent to email are transferred via external email services. Data to the external email services are sent authenticated via TLS protocol. Y Soft uses Twilio SendGrid and Amazon Simple Email Service as external email services. The external email services use the TLS, DKIM, and SPF protocols to deliver the emails securely. |
|
|
Print job metadata: Edge device to cloud |
Print job metadata is used for reporting purposes. Reports provide insight and an audit of print services use. Metadata includes print, copy, and scan activity on printers or groups of printers, users, or groups of users. It does not include the content of a document. |
|
Data Access Permissions & Limitations |
RBAC |
Access to customer data is limited to authorized Y Soft or Y Soft partner reseller employees who require it for their job and whose data access is logged, and who have access only in specific cases. Secure portal communication between an administrator and the SAFEQ Cloud Web UI using TLS/HTTPS, compatible with the version supported by the client. SAFEQ Cloud may authenticate a user’s identity at the print device by verifying against a company’s directory. The device connects to Active Directory using an LDAP (Lightweight Directory Access Protocol) connector on the Edge device synchronized to the cloud service via a secured line. The product does not access any user passwords or other private data. For cloud directories (Microsoft Entra ID, Google, …), standard OAUTH2 protocols are used. Secured separation between tenants’ User Directories is in place for shared infrastructure customers. |
|
|
SSO |
The use of Single Sign-on (SSO) allows you to authenticate users in your own systems without requiring them to enter additional login credentials to use SAFEQ Cloud. |
|
|
Internet security protocols |
Browser access to the SAFEQ Cloud Web Ul is through HTTPS, using role-based access within the application, authenticated via SAML, OAUTH2, and OpenID Connect industry standards. |
|
|
Cloud SQL Database (metadata) |
Application metadata, configuration, job metadata, reporting, and generic user information are stored in the cloud provider’s managed SQL database. A very limited number of highly trained specialists responsible for application maintenance and management on an as-needed basis have administrator access to the databases. Access to the data is logged in the cloud provider’s audit logs. |
|
|
Application Logs |
Application logs for troubleshooting are collected in the cloud provider’s central log repository and available to support personnel on a need-to-know basis. Logs do not expose any access/credentials or document content information. |
|
|
Customer (tenant) specific metadata (users, devices, reporting, print job information, …) |
Role-based administrator access allows management of devices and system reports from the Web UI. This access can be assigned to the customer administrator and/or maintained by a certified Y Soft partner/reseller. Access to the customer application Web UI is limited to support personnel on an as-needed basis. For (alternative) shared infrastructure deployments, a set of support accounts is granted only to a very limited number of highly trained specialists responsible for application maintenance and management on an as-needed basis. Access to the data is logged in the cloud provider’s audit logs. |
|
|
Application / Edge Device Updates |
Edge device application is managed by industry-standard tools, protocols, and systems provided by the cloud provider platform. Deployment is managed via a tiered environment with separated development, testing, staging, and production environment, plus dedicated deployment plans per customer. Updates are deployed via encrypted and device-authenticated HTTP/S communication. Application components are stored in cloud provider’s secured artifact repository and deployed to cloud instances and Edge devices using automated and secured state-of-the are tools (also provided by the cloud platform). All artifacts are created and deployed using a secured development lifecycle process and managed by a team of highly trained specialists responsible for application maintenance and management |
|
Data Retention |
Print/Scan document data |
Print documents are stored only until released on printer or deleted after 7 days if not collected. Scan documents (if targeted for download) are stored until collected by user or deleted after 7 days if not collected. |
|
|
Tenants and metadata |
Tenant data are deleted after license expiration after 90 days for trial licenses and 90 days for production licenses. |
|
|
Users |
Any user metadata are kept until tenant is removed or until deleted by administrator via web interface or external API. |
|
|
Log files and backups |
Any data in log files, audit logs and backups are kept for 90 days and then removed. |
|
Shared Infrastructure |
Shared Infrastructure |
One feature of shared infrastructure that makes it attractive to businesses is its low cost. This is due, in part, to servers managed by the service provider and the sharing of an underlying cloud-based application. The cloud-based application, in this case, SAFEQ Cloud provides services to multiple businesses, each one considered a separate ‘tenant.’ In this multitenant scenario, each tenant must have its own metadata identification, separation, and protection All the above-mentioned points apply. Each tenant owns a unique security certificate associated with its metadata. |
User Identity Management
SAFEQ Cloud is built on modern authentication methods (OAuth 2.0) and utilizes Single sign-on (SSO) provided by external Identity Providers such as Microsoft Entra ID. SSO is a session and user authentication service that permits users to use one set of login credentials to access multiple applications. We recommend that customers who want to use SAFEQ Cloud use an external Identity Provider that manages the Internet identity of all their users. This approach allows admins to define the required level of user identity protection by enforcing multi-factor authentication. Another advantage is that users log in at browsers that they know (and consider secure) via Microsoft's authentication page, and SAFEQ Cloud merely receives information on the results. User credentials are safely confirmed by their external Identity Provider and never shared with the service provider (SAFEQ Cloud). The external Identity Provider provides SAFEQ Cloud with only basic user details such as their first name, last name, and username based on permissions and grants set in the Identity Provider
At MFDs, the users use cards and card readers to authenticate. Upon their first card authentication at the MFD, users are asked to confirm their identity so that the cards may be permanently assigned to their accounts.
Whenever a user logs in, SAFEQ Cloud refreshes the user details from the external Identity Provider – role membership changes, name changes, and account deactivation/reactivation.
The Shared Security Responsibilities
Y Soft and its Partners are jointly responsible for securing their customers’ print infrastructure.
Hosted by Y Soft
In this scenario, Y Soft is responsible for the security of the underlying cloud service platform, network connectivity of the application, and physical data centers. Partners/customers are responsible for user management, account management, and data governance and rights management.
The shared security responsibility model differs from the typical security model a customer would see in an on-premises print environment. By using Y Soft's Cloud infrastructure, customers can leverage the underlying security, integrity & availability that SAFEQ Cloud provides, attaining a higher level of security relative to the investment required when managing the environment themselves.
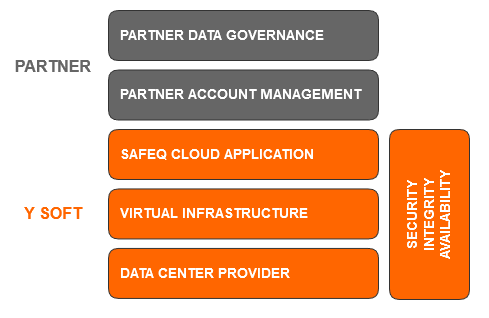
Security responsibilities of Y Soft
In general, Y Soft is responsible for the security of its Virtual infrastructure, OS, and cloud services/products, and provides customers with the technical means necessary to protect their print service.
Y Soft ensures the cloud platform security by:
-
Protecting the physical security of cloud data centers by outsourcing this to best-in-class vendors.
-
Protecting the security of software, and network of the cloud platform by means of OS- and database-patch management, network access control, Anti-DDoS, and disaster recovery, etc.
-
Identifying and fixing security vulnerabilities of the Application or the Cloud service in a timely manner without affecting partners'/customers' service availability.
-
Cooperating with independent third-party security regulation to evaluate security and compliance of Y Soft cloud service security
-
In Y Soft-hosted solutions, data is hosted by major third parties, who have a contractual obligation with us, ensuring they handle data according to GDPR requirements.
Security responsibility for Partners/Customers
Y Soft Partners/Customers (Data Controller) are required to meet strict safety and security demands, and these requirements naturally involve handling documents through SAFEQ Cloud. We see this as an opportunity and take on a proactive approach to fulfilling our duties, thereby helping you fulfill yours. This section describes individual actions that foster data security during the SAFEQ Cloud lifecycle:
-
Y Soft will never use personal data for any other purpose than delivering the SAFEQ Cloud service. Further, it is ensured that any present and future sub-suppliers uphold local or regional data protection laws. For example, this means all data is stored on servers within one region, unless otherwise explicitly agreed upon.
-
The Partner administrator or Customer administrator may however choose to retain the document in SAFEQ Cloud for a predefined number of minutes/hours hereafter – for example, to enable re-print. This will not impose a major security risk, other than more data is available in case of a breach.
Y Soft security and risk management objectives
-
We have developed our security framework using best practices in the SaaS industry. Our key objectives include Customer Trust and Protection – consistently delivering superior product and service to our customers while protecting the privacy and confidentiality of their information.
-
Availability and Continuity of Service – ensure ongoing availability of the service and data to all authorized individuals and proactively minimize the security risks threatening service continuity.
-
Information and Service Integrity – ensure that customer information is never corrupted or inappropriately altered.
-
Compliance with Standards – we design our corporate security program around the industry cybersecurity best practice guidelines including the Center for Internet Security (CIS) Critical Security Controls. Our controls governing the availability, confidentiality, and security of customer data are also designed to be SOC 2 compliant.
Y Soft Security Controls
To protect the data that is entrusted to us, Y Soft utilizes a defense-in-depth approach to implement layers of security controls throughout our organization. The following sections describe a subset of our most frequently asked-about controls.
Y Soft product infrastructure
Cloud Infrastructure Security
Y Soft does not host any SAFEQ Cloud within its corporate offices.
Y Soft outsources the hosting of its product infrastructure to leading cloud infrastructure providers. Our hosting provider guarantees between 99.95% and 100% service availability, ensuring all power, network, and HVAC services redundancy.
Y Soft’s data center infrastructure is available in the USA, Canada, The European Union, the UK, Singapore, and Australia regions. The data center provider maintains an audited security program and physical, environmental, and infrastructure security protections. Business continuity and disaster recovery plans have been independently validated as part of their SOC 2 Type 2 and ISO 27001 certifications.
Our solution has been set up using three different Availability Zones in each region where the solution is deployed. This means we have multiple servers connected in a cluster environment with failover into different physical locations. If one zone fails for any reason, other servers located in a physically different location will automatically take over, completely seamlessly to users.
Our platform regularly undergoes independent verification of security, privacy, and compliance controls, achieving certifications against global standards to ensure it is the most secure in the industry. Recently our environment was assessed by IBM Nordcloud. Their report, “Well-architected review” confirms a high level of operational excellence, security, reliability, and performance efficiency for the SAFEQ Cloud production environment.
Network Security and Perimeter Protection
The Y Soft product infrastructure enforces multiple layers of filtering and inspection of all connections throughout the platform.
Network-level access control lists are implemented to prevent unauthorized network access to our internal product infrastructure. Firewalls are configured to deny network connections that are not explicitly authorized by default, and traffic monitoring is in place to detect anomalous activity.
Changes to our network security are actively monitored and controlled by standard change control processes. Firewall rulesets are reviewed on an annual basis to help ensure that only necessary connections are configured.
To protect our Cloud environment requires the use of several professional tools, including:
-
Security Hub evaluates configuration items to assess whether the resources comply with the desired configurations defined by the defined security standards.
-
GuardDuty which is a threat detection service that continuously monitors for malicious activity and unauthorized behaviors to protect the account.
-
Inspector tools – an automated security assessment service that helps improve the security and compliance of deployed applications. Inspector tools automatically assess applications for exposure, vulnerabilities, and deviations from best practices.
-
IAM Access Analyzers help us to identify the resources in the organization, such as storage or Identity Access Management roles, that are shared with an external entity. This lets us identify unintended access to our resources and data, which is a security risk.
-
Additionally, we periodically monitor trusted advisor findings to keep best practices for cost management, high availability, security, and performance.
Configuration Management
Automation drives Y Soft’s ability to scale with our customers’ needs. Server instances are tightly controlled from provisioning through de-provisioning, ensuring that deviations from configuration baselines are detected and reverted at a predefined cadence. If a production server deviates or drifts from the baseline configuration, it will be overwritten with the baseline configuration within 30 minutes.
All server-type configurations are embedded in images and configuration files. When the server is built, server-level configuration management is handled using these images and configuration scripts. Changes to the configuration and standard images are managed through a controlled change management process. Each instance type includes its own hardened configuration, depending on the deployment of the instance.
Patch management is handled using automated configuration management tools or by removing server instances that are no longer compliant with the expected baseline and provisioning a replacement instance in its place. Rigorous and automated configuration management is baked into our day-to-day infrastructure processing.
Alerting and Monitoring
We also invest heavily in automated monitoring, alerting, and response capabilities to continuously address potential issues. The Y Soft product infrastructure is instrumented to alert engineers and administrators when anomalies occur. In particular, error rates, abuse scenarios, application attacks, and other anomalies trigger automatic responses and alerts to the appropriate teams for response, investigation, and correction. As unexpected or malicious activities occur, automated systems bring in the right people to rapidly address the issue.
Many automated triggers are also designed into the system to respond immediately to unforeseen situations. Traffic blocking, quarantine, process termination, and similar functions kick in at predefined thresholds to ensure that the Y Soft platform can protect itself against a wide variety of undesirable situations.
OMNI Bridge security and privacy
Operating System security
-
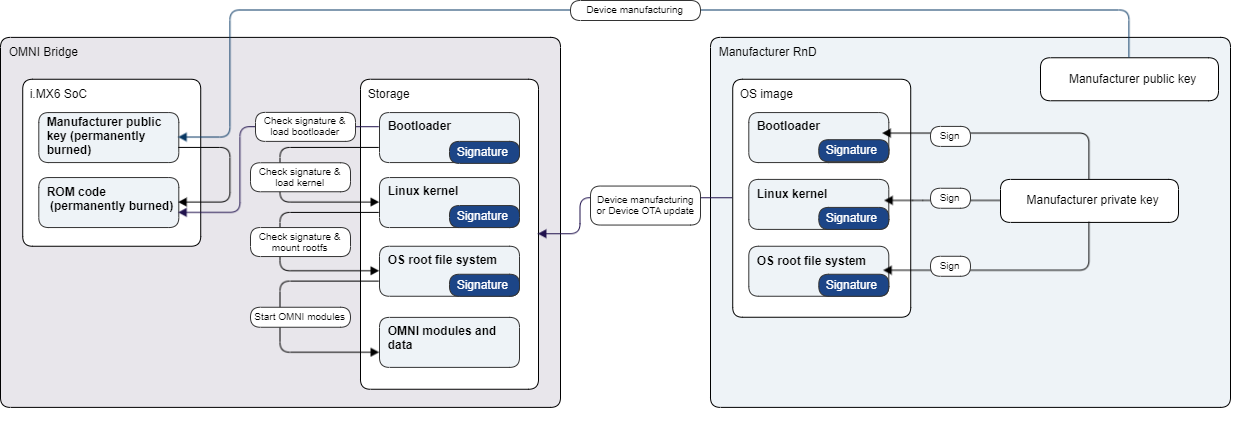
The OMNI Bridge device is designed so that only OS images signed by the manufacturer can be booted on the device.
-
The whole system is based around a security feature of the i.MX6 - High Assurance Boot (HAB)
-
HAB provides a mechanism to establish a chain of trust from HW to the remaining SW components.
-
HW -> bootloader -> kernel -> OS
-
HAB uses public-key cryptography using the RSA algorithm.
-
Public keys are permanently burned to the i.MX6 fuses during device manufacturing.
-
THe OS images are signed, the public key is permanently and immutably burned to the i.MX6 processor in the device.
OMNI Bridge device boot process
-
i.MX6 boot ROM loads and authenticates a bootloader image.
-
Bootloader loads and authenticates kernel image with ramdisk.
-
Init process in ramdisk authenticates the main read-only rootfs image and mounts it.
-
The Init process mounts the read-write data partition.
-
OS boot sequence finished.
-
Starting OMNI modules (applications).
OMNI modules (applications) security
-
All OMNI modules are signed.
-
OS only allows the installation of modules that are signed by official keys.
-
The content of the module image is immutable.
-
Each module runs with a pre-defined set of privileges.
-
Modules run in separate environments.
-
The OMNI Bridge application storage: only authorized apps may access the data. There is no admin access that would be able to access this application data. Having said that, the storage itself is not encrypted for performance reasons. Accessing the stored data would require disassembling the device and desoldering the storage chip. Such operation is not possible without specialized equipment and expert HW skills and will likely result in destroying the OMNI Bridge.
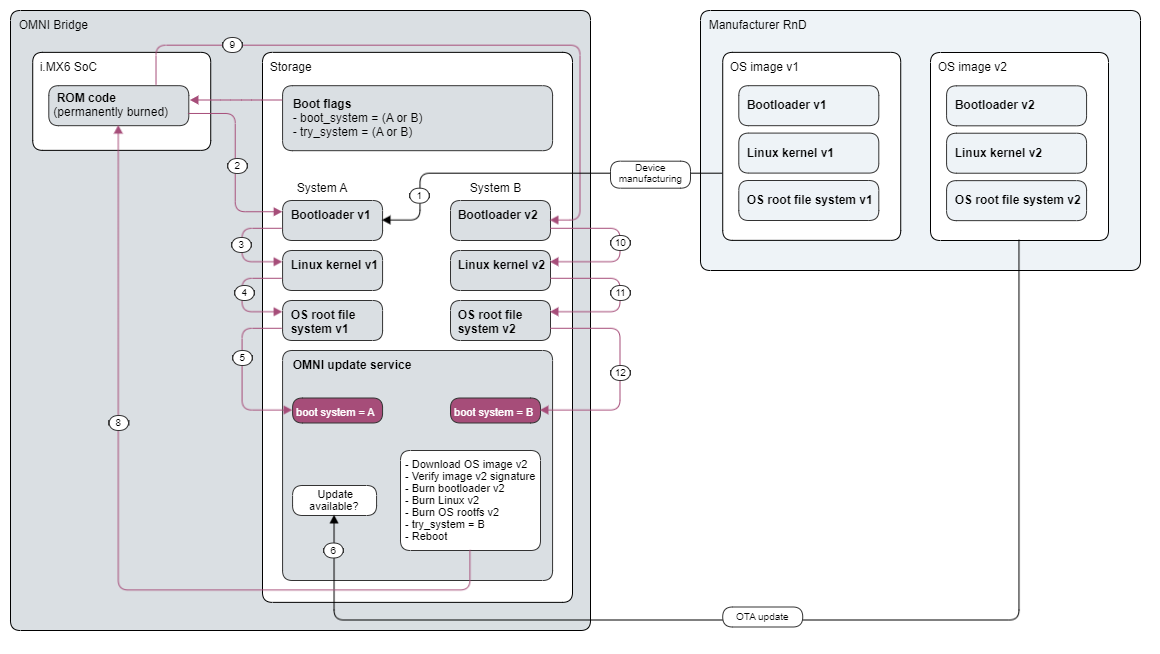
OS update process
-
The operating system on the device can be safely and securely updated.
-
The update mechanism uses a so-called A/B partition scheme for reliability.
-
Each component of the OS is duplicated (bootloader, kernel, OS).
-
In case the update process fails at any stage, the system is reset and boots the previously working OS version.
OS identity and CA
-
Each device has its own identity certificate.
-
The private key never leaves the device; it is held in a blob that could be decrypted only on the given device.
-
The process is based on CAAM (Cryptographic Acceleration and Assurance Module) in the i.MX6 CPU.
-
-
Identity certificates are signed by the manufacturer's CA in the factory.
-
The device can also act as a CA and exposes necessary API
-
The main use is the signing of intermediate certificates for Azure world.
-
OMNI Bridge Factory reset process
-
Factory reset process clears all application and customer data present on the device.
