Relevant Products
SAFEQ Cloud Client configuration is available in PRO PRINT PRO MFD
This configuration is not enabled on SAFEQ Cloud Client installed using the quick installation scenario.
Users can modify several client settings using the configuration dialog:
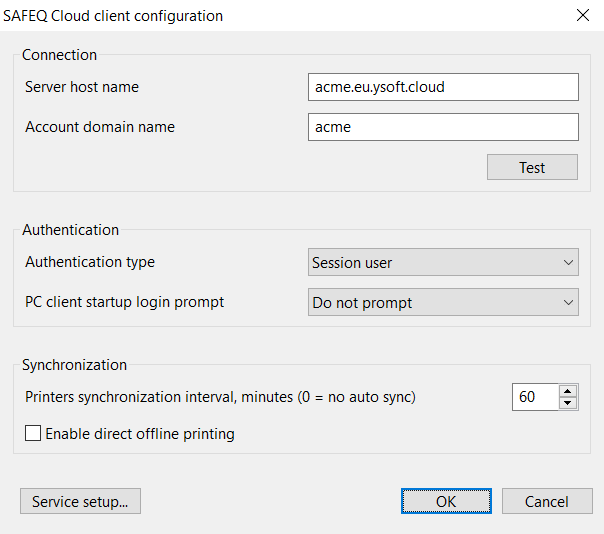
Server host name – host name of the SAFEQ Cloud server or gateway to which the client will connect. If SAFEQ Cloud Client is running in local storage mode this option can only be changed via Service setup button.
Account domain name – domain name of the customer account configured on SAFEQ Cloud server. If not specified it will be inferred from the gateway address setting. If SAFEQ Cloud Client is running in local storage mode this option can only be changed via the Service setup button.
Test – the user is informed about the connection (SAFEQ Cloud gateway address and the account domain name should be accessible in order for the connection to be successful)
Authentication type – currently following authentication types are supported:
-
Session user – username from the current OS session is used for authentication and job sending.
-
Session user + domain – username@ad-domain from the current OS session is used for authentication and job sending. This matches server setting ‘strict domain validation’.
-
Session user principal name – UPN is used for authentication and job sending (whatever UPN configured in user profile, it can be the same as username@ad-domain for simple AD setups).
-
Manual login to SAFEQ Cloud server – The user will be prompted to enter user name and password which will be validated in the SAFEQ Cloud server.
-
Microsoft Azure login (deprecated) – Online authentication is performed against Microsoft Entra ID using OAuth2 workflow. This option is deprecated in favor of “SAFEQ Cloud OAuth2 login”.
-
OpenID Connect login – Perform online authentication against OIDC-compliant identity provider by opening a browser window with OAuth2 workflow. This authentication type supports MFA and requires SAFEQ Cloud server to have at least one authentication provider defined with the type
Client. If a single client-based authentication provider is defined for a given account the user will be redirected to that identity platform. If multiple client-based authentication providers are defined a generic OpenID connect window will be shown prompting the user to enter his or her username. Based on the domain part of the user name the browser will be redirected to the matching identity platform. The following identity platforms are currently supported: Microsoft Entra ID, Google GSuite, Ping Identity. -
SAFEQ Cloud OAuth2 login – Uses a new server login screen with configurable providers for user login.
For this authentication option to work properly, HSTS needs to be disabled for the localhost domain in your browser.
SAFEQ Cloud Client startup login prompt – currently following options are supported after the user restarts the Windows machine:
-
Don’t show – no notification will be shown by the SAFEQ Cloud client
-
Informational popup – the user is asked to login into SAFEQ Cloud Client, “Please login to synchronize printers”
-
Login dialog – the login to print popup appears on the screen, the user is asked to introduce his credentials in order to login into SAFEQ Cloud Client
Automatic refresh period – how often to perform automatic synchronization of the printers, in minutes. When set to 0 automatic refresh will be completely disabled.
Enable direct offline printing – only applies when SAFEQ Cloud Client is running in either Local storage modes.
If SAFEQ Cloud Client loses cloud or primary server connectivity for 10 consecutive minutes it will switch to offline mode. In offline mode SAFEQ Cloud Client will delete any mapped pull queues and instead map direct push print queues to the five most recently used pull printers by SAFEQ Cloud Client logged-in user. When cloud or primary server connection is re-established these offline queues are deleted and any pull queues restored.
Further information:
-
SAFEQ Cloud Client must be running in either Local storage mode, this feature is not compatible with SAFEQ Cloud Client operating in Cloud or Gateway storage modes
-
User's five recently used devices are cached by the client for three days. If a user has not printed for longer than three days prior to offline mode activation, no direct push queues will be mapped
-
As queues are direct push queues, traffic routing from SAFEQ Cloud Client to the printer over standard printing protocols (TCP9100, IPP) is necessary
-
If the user has any direct push queues mapped prior to entering offline mode, these queues are retained in offline mode
-
All printing performed in offline mode is cached and accounted for following reconnection to the cloud or primary server
Service setup – Perform SAFEQ Cloud Client service configuration which requires administrator privileges. This includes: changing between local job storage mode and gateway mode and changing the SAFEQ Cloud server address and domain name in local job storage mode. When pressing this button the user will be prompted with an elevation request.
Options are taken from the system-wide configuration provided during installation. When modified they are stored per user, so it is possible to have multiple user accounts on one PC with different settings.
Note on OKTA and Microsoft Entra ID authentication when using the SAFEQ Cloud Client
For both OKTA and Entra ID authentication providers the supported authentication types are currently “Session + domain name”, “User Principal Name” or “Custom login”.
When custom login is used the user name must be a fully qualified name with “@domain” part which should match the “Domain name” setting in the authentication provider.
Note on client-based authentication with MFA
It is possible to use MFA-enabled authentication against OpenID Connect-compliant identity providers. When this type of authentication is chosen in the configuration a browser window will be opened which will allow to perform online authentication. When authentication is successful the user ID token will be sent to SAFEQ Cloud server. SAFEQ Cloud server should have at least one authentication provider configured with the type Client. The user will then be registered on the server side with an expiration time set according to the token expiration policy configured in the authentication provider.
SAFEQ Cloud Client will attempt to refresh the token periodically and notify the server. When the refresh token expires the user will be logged out. A typical refresh token expiration time is 3 months and usually can be customized in the identity provider settings.
Service setup
Certain SAFEQ Cloud Client settings require service reconfiguration. This can only be done by PC administrator. Reconfiguration is possible either by reinstalling SAFEQ Cloud Client and choosing the relevant settings in the installation dialog or by entering the Service setup from the SAFEQ Cloud Client configuration screen.
Note that pressing this button will show a privilege elevation prompt.
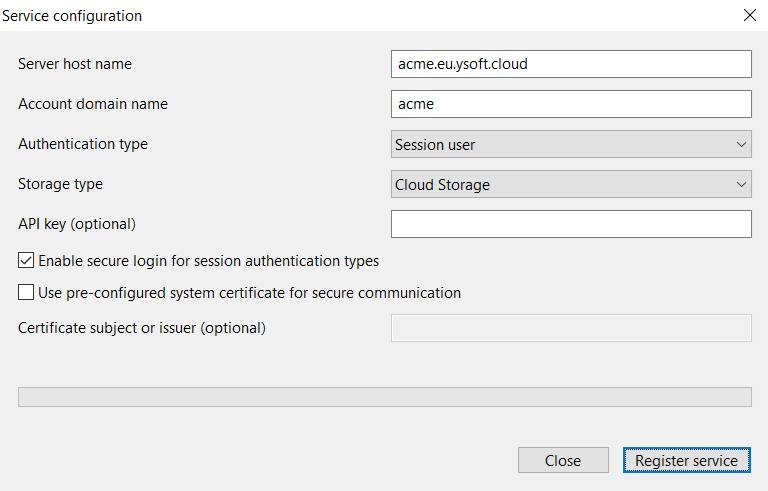
Server host name – host name of SAFEQ Cloud primary server or gateway.
Account domain name – domain name of the account to which this SAFEQ Cloud Client will be connecting. If the account has multiple domains any of them can be specified in this field.
Authentication type – currently following authentication types are supported:
-
Session user – username from the current OS session is used for authentication and job sending (default)
-
Session user + domain – username@ad-domain from the current OS session is used for authentication and job sending. This matches server setting ‘strict domain validation’.
-
Session user principal name – UPN is used for authentication and job sending (whatever UPN configured in user profile, it can be the same as username@ad-domain for simple AD setups).
-
Manual login to SAFEQ Cloud server – The user will be prompted to enter user name and password which will be validated in the SAFEQ Cloud server.
-
Microsoft Azure login (deprecated) – Online authentication is performed against Microsoft Entra ID using OAuth2 workflow. This option is deprecated in favor of “OpenID Connect login”.
-
OpenID Connect login – Perform online authentication against OIDC-compliant identity provider by opening a browser window with OAuth2 workflow. This authentication type supports MFA and requires SAFEQ Cloud server to have at least one authentication provider defined with the type
Client. If a single client-based authentication provider is defined for a given account the user will be redirected to that identity platform. If multiple client-based authentication providers are defined a generic OpenID connect window will be shown prompting the user to enter his or her username. Based on the domain part of the user name the browser will be redirected to the matching identity platform. The following identity platforms are currently supported: Microsoft Entra ID, Google GSuite, Ping Identity.
Storage type – select where SAFEQ Cloud Client stores the data: Cloud storage, Local storage, and Hybrid (direct print locally, secure print to cloud).
API key – API key used to communicate with SAFEQ Cloud server. If this option is not specified the default restricted key will be used. Note that the restricted key may be removed by the server administrator, in this case, a dedicated key must be specified.
Enable secure login for session authentication types – If this option is enabled SAFEQ Cloud Client will be registered as an endpoint and must be authorized by the administrator to use insecure login types (such as Session User or User Principal Name).
Use pre-configured system certificate for secure communication (Windows only) – this option will use the client certificate and key chain from the Windows certificate store when establishing a connection to SAFEQ Cloud server instead of the standard SAFEQ Cloud certificate.
This option is deprecated and will be removed in future versions.
Certificate subject or issuer – an optional field to specify a search pattern for the pre-configured certificate. Only relevant when the Use pre-configured system certificates option is also enabled. A certificate with a matching X.509 subject or issuer will be selected. It is possible to only specify a partial match here, for example, “acme” will select a certificate with “company.acme.com” in a subject or issuer line. If this option is left empty the first available certificate with a private key will be picked up.
Pressing the Register service button will start the registration and configuration process which will be displayed as a progress bar.
Using pre-configured system certificates requires a PKI infrastructure in place and a dedicated SAFEQ Cloud server configuration as described in this section.
