Relevant Products
Authentication providers are available in BREEZE PRINT BREEZE MFD PRO PRINT PRO MFD
Introduction
To log in to SAFEQ Cloud Web UI, submit print jobs, release print jobs on SAFEQ Cloud terminals, use the Mobile app, etc, the users must be authenticated. Use the Authentication providers tab to configure how the users will be authenticated.
SAFEQ Cloud supports two main authentication types:
-
Local user authentication
-
Authentication to external directory via
-
OIDC
-
Service account (Service access)
-
Client-side authentication
-
Users who have been authenticated from the external directory using either a card or a PIN will not be deleted from the SAFEQ Cloud database if the external directory deletes the user. Such cleanup should be executed through the use of API functions.
Their card and/or PIN will also remain assigned to them, which may prevent reusing those credentials for other users (e.g., when companies attempt to reassign cards or PINs of former employees).
Local user authentication
This is the simplest authentication type where the users are created and managed manually in the SAFEQ Cloud server, under the built-in Local authentication provider. By default, there are few users predefined for each created account, including the admin user.
We recommend keeping the local admin user as a fallback login in the case of failure of other authentication methods, such as provider misconfiguration, access token expiration, network issues, or a service disruption on the part of your external authentication provider.
In settings of local provider you have options to change visibility of login form (you can hide username/password and leave only provider buttons) and local provider login button (redirects to login form specific to local provider users, e.g. guests).
Authentication based on OpenID Connect (OIDC)
This type of authentication enables connecting to an external authentication provider through OIDC. SAFEQ Cloud supports the following authentication providers for OIDC:
-
Microsoft Entra ID
-
Google Workspace
-
Okta
We recommend OIDC as the most secure authentication method. It enhances security by redirecting users Web UI and client workstations to the authentication provider's login page, ensuring that credentials are only entered at the provider's site. Furthermore, it eliminates the need for repeated credentials entries and supports multi-factor authentication (MFA).
MFA is only supported for Web UI and client workstations. At the MFD terminal, username and password login works only if MFA is disabled.
OIDC authentication doesn't allow synchronization of card IDs and PINs. If you have this information stored in your authentication provider (instead of directly in SAFEQ Cloud), you may also want to configure service access for the same provider to allow users to log in at the MFD terminal using their company cards and PINs.
Logging in using the OIDC authentication method
When an authentication provider is configured with the OIDC authentication method, users can log in via such authentication provider in two ways:
-
Entering a username matching the authentication provider.
-
Clicking Login via <Provider Name> on the login page.
When a user enters a username that matches the authentication provider with enabled OIDC authentication, they are redirected to the provider's login page, where they authenticate and then are redirected back to SAFEQ Cloud.
When the user clicks Login via <Provider Name>, they are also redirected to the provider's login page.
When configuring the authentication, you will be able to choose whether to show the provider-branded Login via <Provider Name> button on the login page.
User details are synchronized during every user login (either via SAFEQ Cloud Web UI, SAFEQ Cloud Client, MFD terminal, or the Mobile app), except for the user logging in within the lifespan of the existing OIDC Access Token (usually 60 minutes after the first login).
Authentication based on the service access
This authentication method requires you to create a service account in your external authentication provider. This account must have permission to search and retrieve users. SAFEQ Cloud supports the following authentication providers for service access type:
-
Microsoft Entra ID
-
LDAP (including Active Directory)
-
Okta
If you choose this authentication method, you must enter the service account details (e.g., username and password) in the authentication provider settings in SAFEQ Cloud. Users can authenticate against the SAFEQ Cloud server using all available login types: username/password, card ID, and PIN.
We do not recommend using the service access authentication method for authentication providers that support OIDC. Set up OIDC for user login to SAFEQ Cloud Web UI and SAFEQ Cloud Client, and if you need users to log in via company cards or PINs stored in your authentication provider, set up the service access authentication in conjunction with OIDC.
Microsoft Entra ID and LDAP do not support multi-factor authentication (MFA). Also, the Okta MFA support is very limited when using service access authentication only. In these cases, we strongly recommend using OIDC authentication.
Client-side authentication
This type of authentication requires SAFEQ Cloud Client software, which uses interactive browser-based authentication provided by the external authentication provider. You don't need to create service access. MFA is fully supported.
The limitation of this authentication type is that users cannot log in at SAFEQ Cloud terminals via username and password, card IDs, and PINs stored in the authentication provider. Only local card ID and PIN logins are supported. However, users can log in via the one-time passwords (OTPs) functionality. This is useful, for example, for local card registration. You can generate OTPs manually in the Web UI or automatically by setting up triggers. See the section on My profile for more information.
The SAFEQ Cloud Client automatically refreshes information about users from external authentication providers at periodic intervals. After a successful refresh, the user can log in at the MFD for a time defined in the user expiration policy in the authentication provider. If the SAFEQ Cloud Client is offline (or hasn't successfully refreshed information from the external authentication provider), and the time defined in the user expiration policy has passed, the user won't be able to log in at the MFD.
Authentication configuration
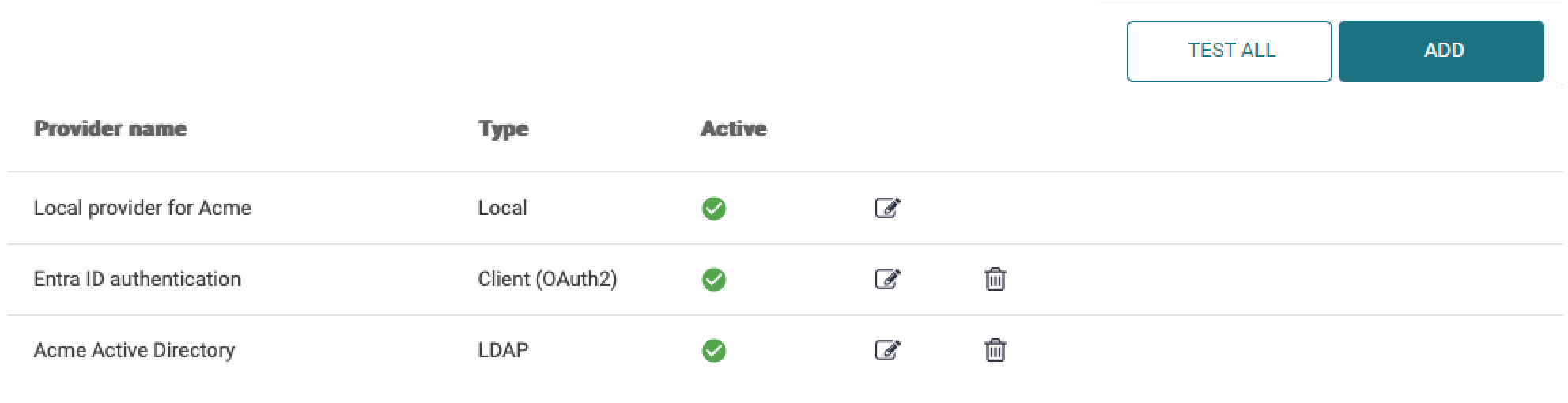
The following authentication provider types are available:
-
Local – Local authentication provider. It will authenticate users against the internal user database in SAFEQ Cloud.
-
LDAP – LDAP authentication provider enables authentication using LDAP/LDAPS against Active Directory, Novell eDirectory, and IBM Domino.
-
Microsoft Entra ID – Microsoft Entra authentication enables authentication against Microsoft Entra ID. See Microsoft Entra authentication.
-
OKTA – OKTA authentication enables integration with the OKTA authentication service. See OKTA Authentication.
-
Client – Client authentication is a special type of authentication performed by the SAFEQ Cloud Client on the client side. See Client authentication.
-
External – SAFEQ Cloud supports external authentication providers where external authentication service such as External Card Repository is used to identify users from different authentication providers.
A newly created vendor or customer accounts always have the Local Authentication Provider added by default. It cannot be removed.
There is no limit to the number of authentication providers you can add.
You can define a priority number for every provider (a higher number means higher priority), which is used for every logical operation where the order of providers matters.
Warning: In a production environment where numerous users are enrolled in the system, deleting an Authentication Provider will result in users' information not being available anymore for authentication, retrieving card numbers, PINs, etc., as user records are bound to the Authentication provider ID that was used when adding them to the database.
See additional instructions for configuring specific authentication providers:
